Openssl Command To Generate Csr And Key
- How To Generate Csr
- Openssl Command To Generate Csr And Key West
- Openssl Windows Create Csr
- Openssl Generate Cert From Csr
- Oct 25, 2019 Common OpenSSL Commands with Keys and Certificates. Generate RSA private key with certificate in a single command openssl req -x509 -newkey rsa:4096 -sha256 -keyout example.key -out example.crt -subj '/CN=example.com' -days 3650 -passout pass:foobar Generate Certificate Signing Request (CSR) from private key with passphrase.
- OpenSSL CSR Wizard. Our OpenSSL CSR Wizard is the fastest way to create your CSR for Apache (or any platform) using OpenSSL. Fill in the details, click Generate, then paste your customized OpenSSL CSR command in to your terminal. Note: After 2015, certificates for internal names will no longer be trusted.
- May 22, 2019 A Certificate Signing Request (CSR) is the first step in setting up an SSL Certificate on your website. SSL certificates are provided by Certificate Authorities (CA), which require a Certificate Signing Request (CSR). This guide will instruct you on how to generate a Certificate Signing Request using OpenSSL.
See Example: SSL Certificate - Generate a Key and CSR. Tableau Server uses Apache, which includes OpenSSL. You can use the OpenSSL toolkit to generate a key file and Certificate Signing Request (CSR) which can then be used to obtain a signed SSL certificate. Steps to generate a key and CSR. I am using the following command in order to generate a CSR together with a private key by using OpenSSL: openssl req -new -subj '/CN=sample.myhost.com' -out newcsr.csr -nodes -sha512 -newkey rsa. Generate CSR - OpenSSL Introduction. This article provides step-by-step instructions for generating a Certificate Signing Request (CSR) in OpenSSL. This is most commonly required for web servers such as Apache HTTP Server and NGINX. If this is not the solution you are looking for, please search for your solution in the search bar above.
Introduction
A Certificate Signing Request (CSR) is the first step in setting up an SSL Certificate on your website. SSL certificates are provided by Certificate Authorities (CA), which require a Certificate Signing Request (CSR).
This guide will instruct you on how to generate a Certificate Signing Request using OpenSSL.
- Access to a user account with root or sudo privileges
- A command line/terminal window
- If you’re working on a remote server, an established SSH connection to the server
- OpenSSL needs to be installed on your system to generate the key
- A text editor, such as nano, to view your key
Open a terminal window. Use your SSH connection to log into your remote server.
Note: If you are working locally, you don’t need an SSH connection. Also, most Linux systems will launch a terminal window by pressing Ctrl-Alt-T or Ctrl-Alt-F1.
Step 2: Create an RSA Private Key and CSR
It is advised to issue a new private key each time you generate a CSR. Hence, the steps below instruct on how to generate both the private key and the CSR.

Make sure to replace your_domain with the actual domain you’re generating a CSR for.
The commands are broken out as follows:
- openssl – activates the OpenSSL software
- req – indicates that we want a CSR
- –new –newkey – generate a new key
- rsa:2048 – generate a 2048-bit RSA mathematical key
- –nodes – no DES, meaning do not encrypt the private key in a PKCS#12 file
- –keyout – indicates the domain you’re generating a key for
- –out – specifies the name of the file your CSR will be saved as
Note: Use 2048-bit key pairs. The 4096-bit key pairs are more secure, however, they require a lot more server resources.
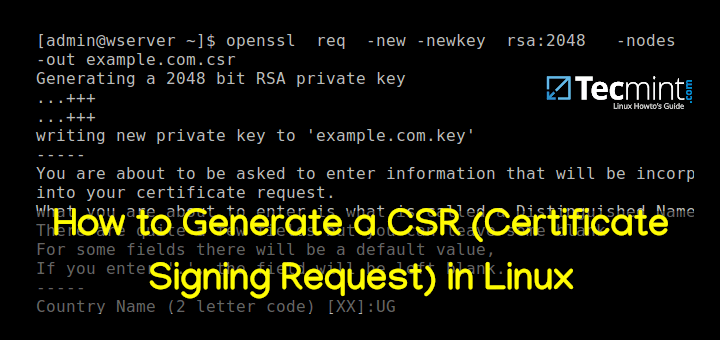
Your system should launch a text-based questionnaire for you to fill out.
Enter your information in the fields as follows:
- Country Name – use a 2-letter country code (US for the United States)
- State – the state in which the domain owner is incorporated
- Locality – the city in which the domain owner is incorporated
- Organization name – the legal entity that owns the domain
- Organizational unit name – the name of the department or group in your organization that deals with certificates
- Common name – typically the fully qualified domain name (FQDN), i.e. what the users type in a web browser to navigate to your website
- Email address – the webmaster’s email address
- Challenge password – an optional password for your key pair
Please take into account that Organization Name and Unit Name must not contain the following characters:
 Use Keygen, generate Generals Zero Hour CD Key. It is designed to be easy to use, so to be available to as many users. It is designed to be easy to use, so to be available to as many users. It has possibility of automatic updates, one hundred percent safe to use and can be used on any system, it is compatible with all Windows.
Use Keygen, generate Generals Zero Hour CD Key. It is designed to be easy to use, so to be available to as many users. It is designed to be easy to use, so to be available to as many users. It has possibility of automatic updates, one hundred percent safe to use and can be used on any system, it is compatible with all Windows.
< > ~ ! @ # $ % ^ * / ( ) ?.,&
Once the software finishes, you should be able to find the CSR file in your working directory.
You can also enter the following:
How To Generate Csr
The system should list out all certificate signing requests on the system. The one that matches the domain name you provided in Step 2 appended with the .csr extension is the one you need to look into. Generate private ssh key from public.
Step 5: Submit the CSR as Part of Your SSL Request
Openssl Command To Generate Csr And Key West
You can open the .csr file in a text editor to find the alphanumeric code that was generated.
Enter the following command:
This text can be copied and pasted into a submittal form to request your SSL certificate from a Certificate Authority.
Make sure you copy the entire text. Some CAs may allow you to simply upload the .csr file you generated. Below is an example of a CSR.
You needn’t send the private key to the CA. Once you get your SSL certificate, the private key on the server will bind with it to encrypt communication.
Now you know how to generate an OpenSSL certificate signing request. Before submitting the CSR to a certificate authority, we recommend verifying the information it holds. Use one of the widely available online CSR decoders.
SSL is a crucial protocol for securing traffic between a website and its visitors. It helps to protect sensitive information online, such as credit card data.
Openssl Windows Create Csr
Next, You Should Also Read:
What is a SAN
A SAN is a Subject Alternative Name, and as the name implies it serves as a secondary (or tertiary, etc.) DNS name that your web application could be identified as. This is useful in the context of web farms behind a reverse proxy, load-balancing solutions, etc.
For example:
Modern Browsers will show an SSL certificate as invalid if a proper SAN is not included, so it’s best practice for us to be in the habit of including SANs in our CSRs.
How to include a SAN
Because we want to include a SAN (Subject Alternative Name) in our CSR (and certificate), we need to use a customized openssl.cnf file.
Openssl Generate Cert From Csr
While you could edit the ‘openssl req’ command on-the-fly with a tool like ‘sed’ to make the necessary changes to the openssl.cnf file, I will walk through the step of manually updating the file for clarity.
Example openssl.cnf file
Note that the subjectAltName declaration calls an array called @alt_names, which is defined at the bottom of the file.
To include a single SAN in your CSR, update the ‘DNS’ declaration to the appropriate value (in this example, ‘webserver1.scriptech.io’), and leave the DNS.x declarations commented out (#). The result is an @alt_names array with a single entry.
To include multiple SANS in your CSR, comment out (#) the ‘DNS’ declaration, and uncomment the DNS.x declarations that you need. For example, your [alt_names] section would look like:
The result is an @alt_names array with multiple entries.
Generate the new key and CSR
If you have not already, copy the contents of the example openssl.cnf file above into a file called ‘openssl.cnf’ somewhere. Make note of the location.
Also make sure you update the DN information (Country, State, etc.)
Create a new key
Create a new CSR
Verify the CSR
To view the contents of your new CSR, use the following command:
This example shows a single SAN which I included in my openssl.cnf file.
Sign the CSR
Now that you have your properly-formatted CSR, you need to sign it using a Trusted Root Certificate Authority. Depending on your context, this could be a third-party CA like DigiCert or GoDaddy, or it could be an internal Certificate Authority (OpenSSL CA, Active Directory Certificate Services)
The contents of a certificate in the openssl format can be viewed with the following command: