Manage Encryption Keys Permission Must Generate A Tenant Secret
- Manage Encryption Keys Permission Must Generate A Tenant Secret Code
- Manage Encryption Keys Permission Must Generate A Tenant Secret Card
- Manage Encryption Keys Permission Must Generate A Tenant Secret Number
- Manage Encryption Keys Permission Must Generate A Tenant Secretary Of State
- Manage Encryption Keys Permission Must Generate A Tenant Secret Account
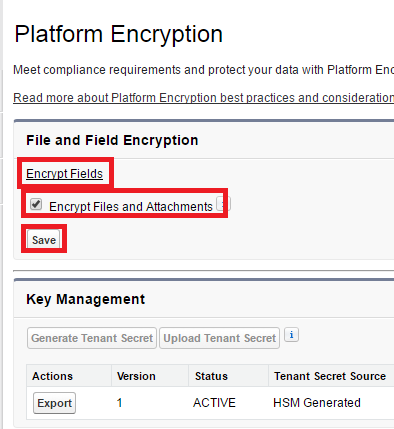
Oct 22, 2015 You can rotate them once a day if you want. Only someone with the Manage Encryption Keys user permission can do this. The Tenant Secret is what makes your derived encryption key unique to your org. So how do we go from a two separately managed secrets to a derived key? Let’s start with the Key Derivation Servers. Grant Manage Encryption Keys to the Encryption Admin (Spring '16): Permission Set or Profile. Go to Setup and search for ‘Encrypt’ Select Platform Encryption. Click Generate Tenant Secret. Select Encrypted Fields. Select all possible fields and Save. Click on Back to Platform Encryption. Enable Files and Attachments Encryption. Jul 20, 2015 The Key Management section allows a user with the Manage Encryption Keys permission (on their profile or via a permission set) to manage Tenant Secrets, one of the 3 inputs to deriving the.
-->Azure App Configuration encrypts sensitive information at rest. The use of customer-managed keys provides enhanced data protection by allowing you to manage your encryption keys. When managed key encryption is used, all sensitive information in App Configuration is encrypted with a user-provided Azure Key Vault key. This provides the ability to rotate the encryption key on demand. It also provides the ability to revoke Azure App Configuration's access to sensitive information by revoking the App Configuration instance's access to the key.
Overview
Azure App Configuration encrypts sensitive information at rest using a 256-bit AES encryption key provided by Microsoft. Every App Configuration instance has its own encryption key managed by the service and used to encrypt sensitive information. Sensitive information includes the values found in key-value pairs. When customer-managed key capability is enabled, App Configuration uses a managed identity assigned to the App Configuration instance to authenticate with Azure Active Directory. The managed identity then calls Azure Key Vault and wraps the App Configuration instance's encryption key. The wrapped encryption key is then stored and the unwrapped encryption key is cached within App Configuration for one hour. App Configuration refreshes the unwrapped version of the App Configuration instance's encryption key hourly. This ensures availability under normal operating conditions.
Manage Encryption Keys Permission Must Generate A Tenant Secret Code
Important
If the identity assigned to the App Configuration instance is no longer authorized to unwrap the instance's encryption key, or if the managed key is permanently deleted, then it will no longer be possible to decrypt sensitive information stored in the App Configuration instance. Using Azure Key Vault's soft delete function mitigates the chance of accidentally deleting your encryption key.
When users enable the customer managed key capability on their Azure App Configuration instance, they control the service’s ability to access their sensitive information. The managed key serves as a root encryption key. A user can revoke their App Configuration instance’s access to their managed key by changing their key vault access policy. When this access is revoked, App Configuration will lose the ability to decrypt user data within one hour. At this point, the App Configuration instance will forbid all access attempts. This situation is recoverable by granting the service access to the managed key once again. Within one hour, App Configuration will be able to decrypt user data and operate under normal conditions.
Note
All Azure App Configuration data is stored for up to 24 hours in an isolated backup. This includes the unwrapped encryption key. This data is not immediately available to the service or service team. In the event of an emergency restore, Azure App Configuration will re-revoke itself from the managed key data.
Requirements
The following components are required to successfully enable the customer-managed key capability for Azure App Configuration:
- Standard tier Azure App Configuration instance
- Azure Key Vault with soft-delete and purge-protection features enabled
- An RSA or RSA-HSM key within the Key Vault
- The key must not be expired, it must be enabled, and it must have both wrap and unwrap capabilities enabled
Once these resources are configured, two steps remain to allow Azure App Configuration to use the Key Vault key:
- Assign a managed identity to the Azure App Configuration instance
- Grant the identity
GET,WRAP, andUNWRAPpermissions in the target Key Vault's access policy.
Enable customer-managed key encryption for your Azure App Configuration instance
To begin, you will need a properly configured Azure App Configuration instance. If you do not yet have an App Configuration instance available, follow one of these quickstarts to set one up:
Tip
The Azure Cloud Shell is a free interactive shell that you can use to run the command line instructions in this article. It has common Azure tools preinstalled, including the .NET Core SDK. If you are logged in to your Azure subscription, launch your Azure Cloud Shell from shell.azure.com. You can learn more about Azure Cloud Shell by reading our documentation
Create and configure an Azure Key Vault
Create an Azure Key Vault using the Azure CLI. Note that both
vault-nameandresource-group-nameare user-provided and must be unique. We usecontoso-vaultandcontoso-resource-groupin these examples.Enable soft-delete and purge-protection for the Key Vault. Substitute the names of the Key Vault (
contoso-vault) and Resource Group (contoso-resource-group) created in step 1.Create a Key Vault key. Provide a unique
key-namefor this key, and substitute the names of the Key Vault (contoso-vault) created in step 1. Specify whether you preferRSAorRSA-HSMencryption.The output from this command shows the key ID ('kid') for the generated key. Make a note of the key ID to use later in this exercise. The key ID has the form:
https://{my key vault}.vault.azure.net/keys/{key-name}/{Key version}. The key ID has three important components:- Key Vault URI: `https://{my key vault}.vault.azure.net
- Key Vault key name: {Key Name}
- Key Vault key version: {Key version}
Create a system assigned managed identity using the Azure CLI, substituting the name of your App Configuration instance and resource group used in the previous steps. The managed identity will be used to access the managed key. We use
contoso-app-configto illustrate the name of an App Configuration instance:The output of this command includes the principal ID ('principalId') and tenant ID ('tenandId') of the system assigned identity. This will be used to grant the identity access to the managed key.
The managed identity of the Azure App Configuration instance needs access to the key to perform key validation, encryption and decryption. The specific set of actions to which it needs access includes:
GET,WRAP, andUNWRAPfor keys. Granting the access requires the principal ID of the App Configuration instance's managed identity. This value was obtained in the previous step. It is shown below ascontoso-principalId. Grant permission to the managed key using the command line:Once the Azure App Configuration instance can access the managed key, we can enable the customer-managed key capability in the service using the Azure CLI. Recall the following properties recorded during the key creation steps:
key namekey vault URI.
Your Azure App Configuration instance is now configured to use a customer-managed key stored in Azure Key Vault.
Next Steps
In this article, you configured your Azure App Configuration instance to use a customer-managed key for encryption. Learn how to integrate your service with Azure Managed Identities.
-->After you've set up Customer Key for Office 365, you can manage your keys as described in this article. Learn more about Customer Key in the related topics.
Restore Azure Key Vault keys
Before performing a restore, use the recovery capabilities provided by soft delete. All keys that are used with Customer Key are required to have soft delete enabled. Soft delete acts like a recycle bin and allows recovery for up to 90 days without the need to restore. Restore should only be required in extreme or unusual circumstances, for example if the key or key vault is lost. If you must restore a key for use with Customer Key, in Azure PowerShell, run the Restore-AzureKeyVaultKey cmdlet as follows:
For example:
If the key vault already contains a key with the same name, the restore operation fails. Restore-AzKeyVaultKey restores all key versions and all metadata for the key including the key name.
Manage key vault permissions
Several cmdlets are available that enable you to view and, if necessary, remove key vault permissions. You might need to remove permissions, for example, when an employee leaves the team. For each of these tasks, you will use Azure PowerShell. For information about Azure Powershell, see Overview of Azure PowerShell.
To view key vault permissions, run the Get-AzKeyVault cmdlet.
For example:
To remove an administrator's permissions, run the Remove-AzKeyVaultAccessPolicy cmdlet:
For example:
Manage Encryption Keys Permission Must Generate A Tenant Secret Card
Manage data encryption policies (DEPs) with Customer Key
Customer Key handles DEPs differently between the different Office 365 services. For example, you can create a different number of DEPs for the different services.
Exchange Online and Skype for Business: You can create up to 50 DEPs. For instructions, see Create a data encryption policy (DEP) for use with Exchange Online and Skype for Business.
SharePoint Online, OneDrive for Business, and Teams files: A DEP applies to data in one geographic location, also called a geo. If you use the multi-geo feature of Office 365, you can create one DEP per geo. If you are not using multi-geo, you can create one DEP. Normally, you create the DEP when you set up Customer Key. For instructions, see Create a data encryption policy (DEP) for each SharePoint Online and OneDrive for Business geo.
Edited 4/17/2014Anyone here interested in playing Diablo III on PC with a controller? Device: XBOX 360 Controller (wireless)Version 4.0 LS ClickMove Mode (Default)L JOYSTICK - Move 65%: Center + Move MAPPED TO MOUSE SPRINGR JOYSTICK - Move 65%: Center + Move MAPPED TO MOUSE SPRINGBoth Analog Sticks to the same thing but are set to different Ranges, The Right Stick has a short range which is great for looting.L JOYSTICK BTN - ZoomR JOYSTICK BTN - Menu - MapL TRIGGER - Menu Mode Shift-Mode Button (BLUE) ( Shifts to traditional Analog Mouse Mapping instead of Spring RT and RS become Left and Right Mouse buttons. Pinnacle game profiler key generator software.
View the DEPs you've created for Exchange Online and Skype for Business
To view a list of all the DEPs you've created for Exchange Online and Skype for Business using the Get-DataEncryptionPolicy PowerShell cmdlet, complete these steps.
Using a work or school account that has global administrator permissions in your Office 365 organization, connect to Exchange Online PowerShell.
To return all DEPs in your organization, run the Get-DataEncryptionPolicy cmdlet without any parameters.
For more information about the Get-DataEncryptionPolicy cmdlet, see Get-DataEncryptionPolicy.
Assign a DEP before you migrate a mailbox to the cloud
When you assign the DEP, Office 365 encrypts the contents of the mailbox using the assigned DEP during the migration. This process is more efficient than migrating the mailbox, assigning the DEP, and then waiting for encryption to take place, which can take hours or possibly days.
To assign a DEP to a mailbox before you migrate it to Office 365, run the Set-MailUser cmdlet in Exchange Online PowerShell:
Using a work or school account that has global administrator permissions in your Office 365 organization, connect to Exchange Online PowerShell.
Run the Set-MailUser cmdlet.
Where GeneralMailboxOrMailUserIdParameter specifies a mailbox, and DataEncryptionPolicyIdParameter is the ID of the DEP. For more information about the Set-MailUser cmdlet, see Set-MailUser.
Determine the DEP assigned to a mailbox
To determine the DEP assigned to a mailbox, use the Get-MailboxStatistics cmdlet. The cmdlet returns a unique identifier (GUID).
Using a work or school account that has global administrator permissions in your Office 365 organization, connect to Exchange Online PowerShell.
Where GeneralMailboxOrMailUserIdParameter specifies a mailbox and DataEncryptionPolicyID returns the GUID of the DEP. For more information about the Get-MailboxStatistics cmdlet, see Get-MailboxStatistics.
Run the Get-DataEncryptionPolicy cmdlet to find out the friendly name of the DEP to which the mailbox is assigned.
Where GUID is the GUID returned by the Get-MailboxStatistics cmdlet in the previous step.
Verify that Customer Key has finished encryption
Whether you've just rolled a Customer Key, assigned a new DEP, or migrated a mailbox, use the steps in this section to ensure that encryption completes.
Verify encryption completes for Exchange Online and Skype for Business
Encrypting a mailbox can take some time. We recommend that you wait 72 hours before you attempt to validate encryption after you change a DEP or the first time you assign a DEP to a mailbox.
Use the Get-MailboxStatistics cmdlet to determine if a mailbox is encrypted.
The IsEncrypted property returns a value of true if the mailbox is encrypted and a value of false if the mailbox is not encrypted.
The time to complete mailbox moves depends on the size of the mailbox. If Customer Key hasn't completely encrypted the mailbox after 72 hours from the time you assign a new DEP, initiate a mailbox move. To do this, use the New-MoveRequest cmdlet and provide the alias of the mailbox. For example:
For more information about this cmdlet, see Get-MailboxStatistics.
Verify encryption completes for SharePoint Online, OneDrive for Business, and Teams files
Check on the status of encryption by running the Get-SPODataEncryptionPolicy cmdlet as follows:
The output from this cmdlet includes:
The URI of the primary key.
The URI of the secondary key.
The encryption status for the geo. Possible states include:
Unregistered: Customer Key encryption has not yet been applied.
Registering: Customer Key encryption has been applied and your files are in the process of being encrypted. If the key for the geo is registering, you'll also be shown information on what percentage of sites in the geo are complete so that you can monitor encryption progress.
Registered: Customer Key encryption has been applied, and all files in all sites have been encrypted.
Rolling: A key roll is in progress. If the key for the geo is rolling, you'll also be shown information on what percentage of sites have completed the key roll operation so that you can monitor progress.
Revoke your keys and start the data purge path process
You control the revocation of all root keys including the availability key. Customer Key provides control of the exit planning aspect of the regulatory requirements for you. If you decide to revoke your keys to purge your data and exit the service, the service deletes the availability key once the data purge process completes.
Office 365 audits and validates the data purge path. For more information, see the SSAE 18 SOC 2 Report available on the Service Trust Portal. In addition, Microsoft recommends the following documents:
The data purge path differs slightly between the different Office 365 services.
Revoke your Customer Keys and the availability key for Exchange Online and Skype for Business
When you initiate the data purge path for Exchange Online and Skype for Business, you set a permanent data purge request on a DEP. Doing so permanently deletes encrypted data within the mailboxes to which that DEP is assigned.
Manage Encryption Keys Permission Must Generate A Tenant Secret Number
Since you can only run the PowerShell cmdlet against one DEP at a time, consider reassigning a single DEP to all of your mailboxes before you initiate the data purge path.
Manage Encryption Keys Permission Must Generate A Tenant Secretary Of State
Warning
Do not use the data purge path to delete a subset of your mailboxes. This process is only intended for customers who are exiting the service.
To initiate the data purge path, complete these steps:
Remove wrap and unwrap permissions for “O365 Exchange Online” from Azure Key Vaults.
Using a work or school account that has global administrator privileges in your Office 365 organization, connect to Exchange Online PowerShell.
For each DEP that contains mailboxes that you want to delete, run the Set-DataEncryptionPolicy cmdlet as follows.
If the command fails, ensure that you've removed the Exchange Online permissions from both keys in Azure Key Vault as specified earlier in this task. Once you've set the PermanentDataPurgeRequested switch using the Set-DataEncryptionPolicy cmdlet, you'll no longer be able to assign this DEP to mailboxes.
Contact Microsoft support and request the Data Purge eDocument.
At your request, Microsoft sends you a legal document to acknowledge and authorize data deletion. The person in your organization who signed up as an approver in the FastTrack offer during onboarding needs to sign this document. Normally, this is an executive or other designated person in your company who is legally authorized to sign the paperwork on behalf of your organization.
Once your representative has signed the legal document, return it to Microsoft (usually through an eDoc signature).
Once Microsoft receives the legal document, Microsoft runs cmdlets to trigger the data purge which first deletes the policy, marks the mailboxes for permanent deletion, then deletes the availability key. Once the data purge process completes, the data has been purged, is inaccessible to Exchange Online, and is not recoverable.
Revoke your Customer Keys and the availability key for SharePoint Online, OneDrive for Business, and Teams files
Manage Encryption Keys Permission Must Generate A Tenant Secret Account
To initiate the data purge path for SharePoint Online, OneDrive for Business, and Teams files, complete these steps:
Revoke Azure Key Vault access. All key vault admins must agree to revoke access.
You do not delete the Azure Key Vault for SharePoint Online. Key vaults may be shared among several SharePoint Online tenants and DEPs.
Contact Microsoft to delete the availability key.
When you contact Microsoft to delete the availability key, we'll send you a legal document. The person in your organization who signed up as an approver in the FastTrack offer during onboarding needs to sign this document. Normally, this is an executive or other designated person in your company who's legally authorized to sign the paperwork on behalf of your organization.
Once your representative signs the legal document, return it to Microsoft (usually through an eDoc signature).
Once Microsoft receives the legal document, we run cmdlets to trigger the data purge which performs crypto deletion of the tenant key, site key, and all individual per-document keys, irrevocably breaking the key hierarchy. Once the data purge cmdlets complete, your data has been purged.
