Generating A Hash Code From Public And Private Keys
- Generating A Hash Code From Public And Private Keys In Ubuntu 18 04 For Modules
- Generating A Hash Code From Public And Private Keys 2017
Basically, you generate a key pair (private key and public key). The private key is placed on your local machine and the public key is uploaded to the server. When connecting to the server, a validation of these two keys is made and if the key pair passes the validation you are allowed to connect. Dim signedHashValue As Byte 'Generate a public/private key pair. Dim rsa As New RSACryptoServiceProvider 'Create an RSAPKCS1SignatureFormatter object and pass it 'the RSACryptoServiceProvider to transfer the private key. Dim rsaFormatter As New RSAPKCS1SignatureFormatter(rsa) 'Set the hash algorithm to SHA1. Jul 04, 2017 Private key is otherwise called a secret key. At a given point, a sender can make use of 3 keys: sender’s private key, sender’s public key and the receiver’s public key.
Generating A Hash Code From Public And Private Keys In Ubuntu 18 04 For Modules
-->Cryptographic digital signatures use public key algorithms to provide data integrity. When you sign data with a digital signature, someone else can verify the signature, and can prove that the data originated from you and was not altered after you signed it. For more information about digital signatures, see Cryptographic Services.
 Mar 27, 2018 Build your character and choose your adventure in the largest customizable Far Cry game ever! Take control of iconic muscle cars, ATV's, planes and a lot more to engage the cult forces in epic fights. Assassins Creed 3 KEYGEN.rar. Assassin's Creed III Serial Code Generator - KeyGen Installation instructions:. Download Assassin's Creed III Keygen. Unpack Zip file. Far Cry 3 Key Generator is finally available to download. It was really hard to break the codes and access the main game components but our team of professional coders have finally did it. Most of the people who are used to searching game Far Cry 3, already know that the best Far Cry 3 Keygen source.
Mar 27, 2018 Build your character and choose your adventure in the largest customizable Far Cry game ever! Take control of iconic muscle cars, ATV's, planes and a lot more to engage the cult forces in epic fights. Assassins Creed 3 KEYGEN.rar. Assassin's Creed III Serial Code Generator - KeyGen Installation instructions:. Download Assassin's Creed III Keygen. Unpack Zip file. Far Cry 3 Key Generator is finally available to download. It was really hard to break the codes and access the main game components but our team of professional coders have finally did it. Most of the people who are used to searching game Far Cry 3, already know that the best Far Cry 3 Keygen source.
This topic explains how to generate and verify digital signatures using classes in the System.Security.Cryptography namespace.
Generating Signatures
Digital signatures are usually applied to hash values that represent larger data. The following example applies a digital signature to a hash value. First, a new instance of the RSACryptoServiceProvider class is created to generate a public/private key pair. Next, the RSACryptoServiceProvider is passed to a new instance of the RSAPKCS1SignatureFormatter class. This transfers the private key to the RSAPKCS1SignatureFormatter, which actually performs the digital signing. Before you can sign the hash code, you must specify a hash algorithm to use. This example uses the SHA1 algorithm. Finally, the CreateSignature method is called to perform the signing.
Due to collision problems with SHA1, Microsoft recommends SHA256 or better.
Signing XML Files
The .NET Framework provides the System.Security.Cryptography.Xml namespace, which enables you sign XML. Signing XML is important when you want to verify that the XML originates from a certain source. For example, if you are using a stock quote service that uses XML, you can verify the source of the XML if it is signed.
The classes in this namespace follow the XML-Signature Syntax and Processing recommendation from the World Wide Web Consortium.
Verifying Signatures
To verify that data was signed by a particular party, you must have the following information:
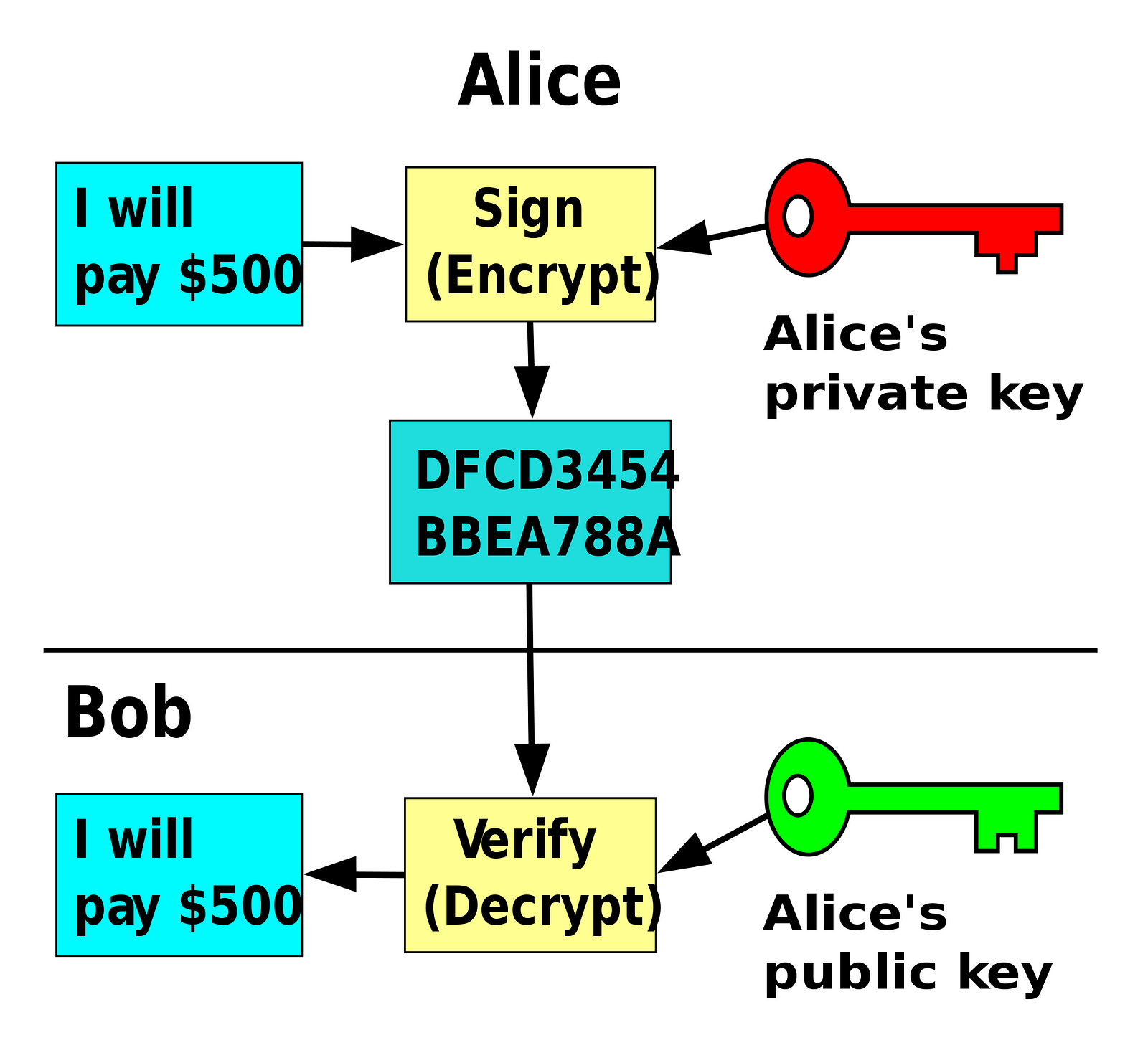
The public key of the party that signed the data.
The digital signature.
The data that was signed.
The hash algorithm used by the signer.
PDF compatibility might help cut back on the expense of permits for additional applications, Read Mode enhances its general usability in reading-heavy tasks or through reading-heavy intervals, and it’s simple enough to adapt to that it doesn’t produce much overhead. You may save the document on the internet and keep editing it in your home or from another pc.Microsoft Office 2013 Crack is excellent. However, its advantages are most significant for medium and huge companies. Microsoft project 2013 product key generator.
To verify a signature signed by the RSAPKCS1SignatureFormatter class, use the RSAPKCS1SignatureDeformatter class. The RSAPKCS1SignatureDeformatter class must be supplied the public key of the signer. You will need the values of the modulus and the exponent to specify the public key. (The party that generated the public/private key pair should provide these values.) First create an RSACryptoServiceProvider object to hold the public key that will verify the signature, and then initialize an RSAParameters structure to the modulus and exponent values that specify the public key.
The following code shows the creation of an RSAParameters structure. The Modulus property is set to the value of a byte array called modulusData and the Exponent property is set to the value of a byte array called exponentData.
Generating A Hash Code From Public And Private Keys 2017
After you have created the RSAParameters object, you can initialize a new instance of the RSACryptoServiceProvider class to the values specified in RSAParameters. The RSACryptoServiceProvider is, in turn, passed to the constructor of an RSAPKCS1SignatureDeformatter to transfer the key.
The following example illustrates this process. In this example, hashValue and signedHashValue are arrays of bytes provided by a remote party. The remote party has signed the hashValue using the SHA1 algorithm, producing the digital signature signedHashValue. The RSAPKCS1SignatureDeformatter.VerifySignature method verifies that the digital signature is valid and was used to sign the hashValue.
This code fragment will display 'The signature is valid' if the signature is valid and 'The signature is not valid' if it is not.